SSU detained a "mole" of the Russian GRU within the ranks of the Territorial Recruitment Center in Volyn
The military counterintelligence of the Security Service, with the assistance of the Ukrainian Armed Forces Command, detained a Russian agent who was preparing a new series of Russian airstrikes on Volyn.
He was identified as a 30-year-old serviceman serving in the security unit of the local TRC. According to case materials, he was remotely recruited by a staff member of Russian military intelligence (better known as GRU).
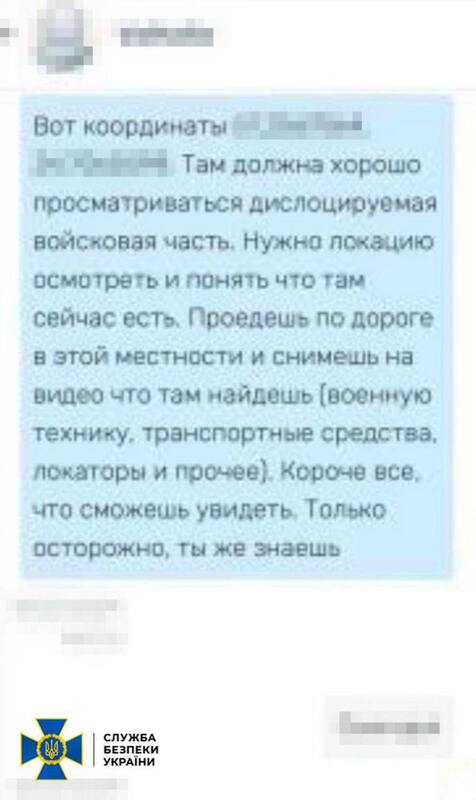
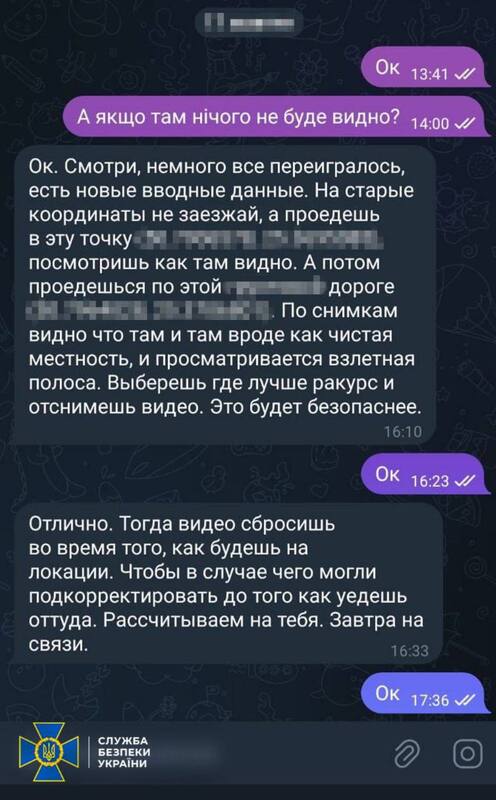
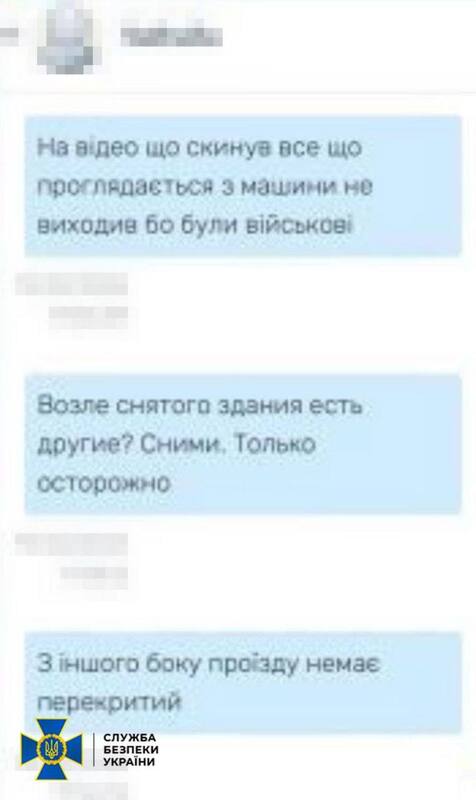
The investigation materials indicate that the individual attempted to locate and transfer to the aggressor the locations of units of the Ukrainian Armed Forces, Security Service, and National Police.
To accomplish this task, the agent used a service vehicle to survey the area under the guise of work trips, recording the location of military objects.
He also attempted to identify radar stations and anti-aircraft missile systems of the Ukrainian Armed Forces in order to facilitate enemy strikes "bypassing" Ukrainian air defense.
The agent sent the obtained information to his Russian handler via an anonymous chat in a messenger app.
The Security Service’s military counterintelligence exposed the Russian agent, documented his crimes, and detained him. Additional measures were also taken to secure the locations of the Defence Forces.
During searches, a mobile phone was seized from the detainee containing evidence of his cooperation with Russia.
According to the investigation, the individual came to the attention of the occupiers through his relatives in Russia, with whom he maintained contact and shared anti-Ukrainian views.
Investigators from the Security Service notified the agent of suspicion under part 2 of Article 111 of the Criminal Code of Ukraine (state treason committed under martial law).
The perpetrator is in custody. He faces life imprisonment with confiscation of property.
The special operation was conducted under the procedural guidance of the Volyn Specialized Defence Prosecution.